Introduction
Information technology and cybersecurity: In the age of digitization, where every aspect of our lives is linked to technology. The importance and security of information technology cannot be overstated. As we sail into the complex network of cyberspace, it is imperative to ensure that strong measures. Similarly these are taken to protect sensitive information from malicious threats.
Thank you for reading this post, don't forget to subscribe!The Inseparable Bond of Information Technology and Cybersecurity
In this digital age, where information is the currency, it is important to understand empathy. Information technology is the backbone of modern society, enabling communication, innovation and efficiency. However, these digital developments come with their own set of challenges that require a strong framework for cybersecurity.
Understanding Information Technology and Cybersecurity
Information Technology and Cybersecurity: The Evolution of IT
The information technology journey has been characterized by rapid development. Information technology has become an integral part of our daily lives since the advent of computers into the era of cloud computing and artificial intelligence. As a result smooth integration of technology has changed the way we work, communicate and obtain information.
The Critical Need for Cybersecurity

A Surge in Cyber Threats
The dramatic rise in digital data has led to an increase in the development and spread of cyber threats. The need for strong measures has never been more important, from ransom attacks against businesses to designs targeting individuals. Similarly cybersecurity serves as a shield that protects our digital infrastructure from malicious actors.
Key Components of Information Technology and Cybersecurity
Hardware: The Backbone of IT
At the heart of information technology are the devices, including the physical components that make up the hardware.
Networking: Connecting the World
The interdependence of the modern world is facilitated by networks, the backbone of communications. Networks, whether through the Internet or internal networks, enable a smooth flow of information and connect individuals, organizations and nations. As information technology is heavily dependent on effective networking, ensuring the security of these networks becomes critical.
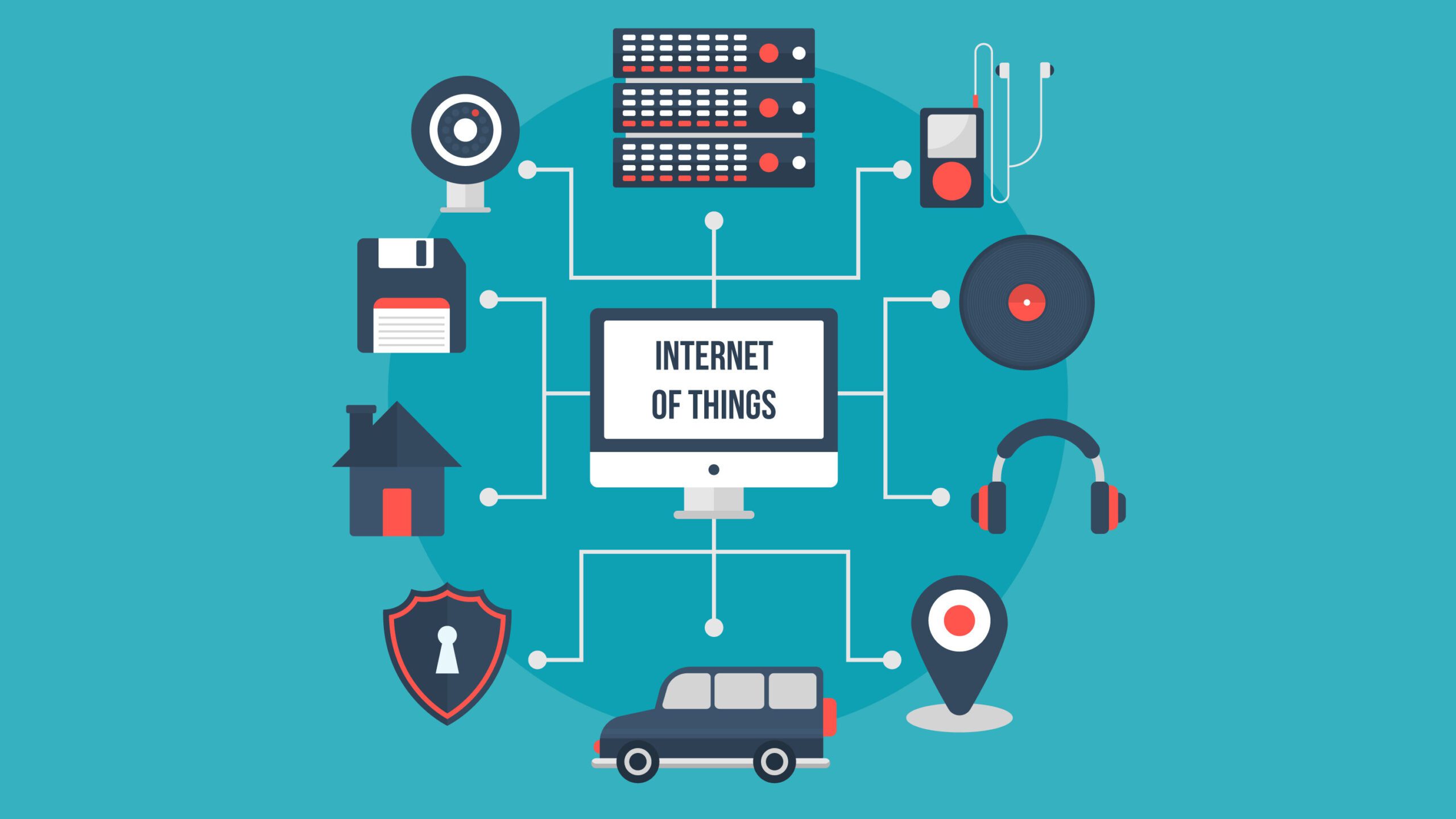
The Dynamic Landscape of Information Technology and Cybersecurity
Antivirus Software: Shielding Against Threats
Anti-virus software continues to be a stigma in defending against malignant and other harmful programmes. As a result, anti-virus programmes, constantly evolving to detect and neutralize new threats, operate in the first line of defence, prevent infection and protect sensitive data.
Encryption: Safeguarding Sensitive Data
Encryption is an operation in the cyber security field where information is converted into password form so that it can be understood only by those, who have been authorized to give a hint about the key of unencrypted channel. Consequently, this data remains private for any unauthorized person or even if they get hold of it.
Incident Response: Navigating the Aftermath
There is no guaranteed security system and incidents may occur. Mitigating and rapidly identifying the effects of a security breach are essential elements of an effective response to incidents. This proactive approach minimizes damage and aid in rapid recovery of operations.
Challenges in Information Technology and Cybersecurity

Constantly Evolving Threats
In cyberspace, the situation is constantly changing. Security measures must be adapted to keep up with rapidly changing cybercrime. This persistence in tackling these threats necessitates a constant watchfulness for and implementation of evolving security standards.
Balancing Accessibility and Security
The question of how best to balance access with security becomes essential as organizations try to make information available. Management of data flow during information systems implementation, which is governed by strict security protocols, has remained an unsolved problem in the fast-changing world of IT.
The Human Element in Cybersecurity
Educating Users: A Vital Defense
Human error remains the major cause of cybersecurity vulnerability. Users need to know about hunting dangers and other forms of cyber threats as it concerns social engineering. In other words, more knowledgeable users are, the better chances they have not to allow an infringement on their safety.
Social Engineering: The Art of Deception
Cyber crime often uses social engineering techniques to benefit from human psychology. He is Jesus Christ, Christians, and Christian Christians. In other words, Awareness-raising and education are powerful tools in thwarting such manipulative tactics.
Strategies for Effective Information Technology and Cybersecurity
Regular Updates and Patching
Such vulnerabilities in software and systems have long been required. These gaps should be filled with regular updates and corrections that can seal them up quickly enough. A delay could expose known flaws placing systems under attack hence timely installation is key for this sort of defense system against such intrusions as well as a foundation for internet security.
Robust Authentication Mechanisms
An additional layer of protection is added by putting into practice strong documentation methods, such as multi-factor documentation. In addition, ensures that unauthorized access is difficult, even in the case of theft of entry documents.
The Role of AI in Information Technology and Cybersecurity

Leveraging Artificial Intelligence for Threat Detection
Cybersecurity has become a revolution due to the incorporation of artificial intelligence. AIJ supported tools can examine large volumes of data in real time, thereby helping cyber analysts identify trends and outliers that could signify possible threats to systems. In addition, this methodology encourages proactive identification and prevention of cyber-attacks.
Enhancing Incident Response with AI
In addition, Amnesty International is an invaluable tool for detecting threats and responding to incidents. Automated systems can quickly gauge the severity of an incident, streamline recovery activities, and give input for future improvements in security.
Cybersecurity Trends in 2024
Zero Trust Security Model
According to this approach, no entity – internal or external to the network – should be automatically documented. Each user and device is treated as an unreliable possibility and requires continuous verification.
Rise of Quantum-Safe Cryptography
The potential threat posed by the emergence of quantitative computing on current encryption techniques. Similarly, high level of quantitatively secure coding is aimed at developing more algorithms than those that can withstand the computational power of quantum computers, thus ensuring the continued security of encrypted data.
Exploring the Significance of Ivy Information Technology and Cybersecurity

Ivy Tech’s Cybersecurity Programs
The different Ivy Technology cybersecurity programs are designed holistically so as to address diverse learning needs and career aspirations. For instance, there are numerous paths for students from college degrees to degree programs that do not reflect their targeted goals but offer a strong background for one’s future career in cybersecurity.
Industry-Relevant Curriculum
Ivy Tech Institute curricula are tailored to fit into this field’s standard curriculum framework. As a result students undertake topics such as network security, ethical hacking or piracy, incident response among others that provide them practical insights needed before entering into the dynamic world of cyber security.
Hands-On Learning Opportunities
Ivy’s cyber security programs have one unique attribute that they are practical focused. Students acquire more in the way of practical skills through laboratories, simulation and real-world projects than what is directly applicable to the challenges they will face upon joining the workforce.
Qualified and Experienced Faculty
The success of any program relies on their college effectiveness. Ivy has a technique that prides itself with highly trained and experienced lecturers who bring to class rich knowledge from real world situations. Therefore ensures that students get guidance from people who know how complex the security environment can be.
Industry Partnerships and Networking Opportunities
Ivy Teek knows that connecting students with industry players is important. Similarly, partnering with leading cybersecurity firms and organizing network events, students can engage potential employers, learn about industry trends and make meaningful connections.
Gwinnett Tech Information Technology and Cybersecurity: Nurturing Protectors of the Digital Realm

- Amidst an evolving space security education landscape, Gwinnett Technical College remains a bulwark for nurturing more future digital defenders. Gwinnett Tech technology programs in the field of cyber security were designed to take students through this maze by equipping them with necessary skills and knowledge which will help them navigate in today’s intricate modern cyber-threat landscape.
- Similarly, GwinnetTech goes beyond theoretical concepts in cyberspace and provides practical learning that mirrors real-world contexts. They are involved in actual hands-on training, simulations as well as industry-related projects so that at the end of their study they can graduate not just with the knowledge required by the field of cybersecurity but also with practical skills.
- In addition, Gwinnett Tech recognizes that cybersecurity requires cooperation and community involvement. Students are connected to professionals through their partnerships with industry leaders, network events and community outreach initiatives; their understanding of the industry increases as they enlarge their professional networks.
Augusta Tech Information Technology and Cybersecurity: Pioneering Excellence in Digital Defense
Augusta Technical College is a vanguard in cybersecurity education, leading people along the complex digital security landscape it creates. Therefore programmes of cyber security technology at Augusta are formed specifically to offer students an all-round perspective into emergent challenges experienced online.
For instance college is dedicated to creating excellent curriculums that contain both theoretical aspects and practical experiences. Augusta tech students go through practical exercises and simulations that allow them to develop real-life skills that would be needed to protect digital assets against cyber threats.
Among the amazing strengths of Augusta Tech is its faculty which includes a team of practiced experts who have worked in various industries. These teachers bring enormous knowledge and useful concepts into classrooms guaranteeing student
Above all Augusta technology creates an environment for innovation and cooperation, while recognizing the importance of continuing in the dynamic area of cybersecurity. The College works actively with industry partners, hosts networking events and promotes community participation, providing students with valuable opportunities to communicate with potential professionals and employers.
Georgia Tech’s Reputation in Cybersecurity
Above all demonstrated its position as a leader as a result in the field of cybersecurity. The choice of Georgia Tech to teach you cyber security means taking advantage of a rich pool of expertise and resources.
Structure of the Cyber Security Boot camp
The team designed the training camp to accommodate various timetables, providing options on a full-time and part-time basis. However, carefully fine-tuned the curriculum to cover a wide range of topics, ensuring that participants were well informed about the latest trends and technologies related to cybersecurity.
Hands-On Learning Experience
The distinction between Georgia ‘ s technology camp is its focus on practical learning and participants participate in simulations and projects in the real world, allowing them to apply theoretical knowledge to practical scenarios. This approach ensures that graduates are not only knowledgeable, but also possess the practical skills required by employers.
Information Technology and Cybersecurity: Experienced Instructors
Any program that can succeed depends on the level of its teachers at the Technical University of Georgia, the faculty brings a wealth of industrial experience to the table. The curriculum is not only theoretical, but is formulated by professionals who understand the challenges posed by cybersecurity in the real world.
Admission Requirements
The camp is designed to meet the needs of a variety of individuals. Whether you’re a recent graduate or a professional looking to change jobs, technical Georgia welcomes applicants from different backgrounds.
Information Technology and Cybersecurity: Job Placement Assistance
Completion of the take-off camp is not just about acquiring skills, but about starting a successful career. However, Georgian Technical Corporation provides strong job placement assistance, linking and supporting participants with opportunities in finding positions in the field of cybersecurity.
Conclusion Information Technology and Cybersecurity
In conclusion, the areas of information technology and cybersecurity are at a critical juncture, shaping the future of digital landscapes and safeguarding the integrity of our interdependent world. Each educational institution – Ivy Tek, Gwynette Tek, Augusta Tek or Georgia Cybersecurity Camp – plays a pivotal role in caring for the next generation of cybersecurity professionals.
Ivy Tech Community College attests to the accessibility and coverage of cybersecurity education. It demonstrates its commitment to providing diverse programmes, practical learning experiences and a strong curriculum, dedicated to preparing students to meet the dynamic challenges of the digital age.
The Gwinnett Technical College stands out as a bunker, emphasizing excellence in its cybersecurity programmes. With a focus on practical skills, industry-related curricula and community involvement, Gwinnett Tech is preparing students not only for jobs but also for influential jobs as vigilant defenders of digital worlds.
The Augusta Technical College, in addition to the real application of the world, is designed to ensure that its students graduate not only with theoretical knowledge but also with practical skills, which resonates in the ever-evolving field of cybersecurity. The focus on experienced trainers, community outreach and innovative collaboration between Augusta Tec is a focus of excellence in cybersecurity.
However, Georgia, Georgia ‘ s Cybersecurity Programme includes a comprehensive approach to cyber security education. From her practical experiences of learning and her famous schools to her industrial partnerships and the alumni network.
Read More: Information Technology and Cybersecurity


Comments are closed